Attack Vector: Mobile Routers - Pwning SIM Numbers
Background
Mobile routers come in different shapes, size, could be portable or stationary. They are very convenient for home users and businesses too.
They are a very interesting IoT attack vector due to their capabilities and the way they operate. The mobile routers we researched require a SIM card to facilitate internet access. In Kuwait, to pay for the service, usually you must know the mobile number associated with the SIM card which is handed to you by the operator. These mobile numbers can receive and sometimes send SMS messages.
Attack Vector
The mobile routers we came across have an administration web panel. Some web panels include a feature which allows the user to view and send SMS messages.
We will be looking into the possibility for attackers to obtain SIM card numbers.

Should an attacker gain unauthorized access to the web panel, they will be able to view SMS messages recieved to the number tied to the SIM card inserted in the mobile router. Surely, for this feature to be abused the attacker will need to:
- Gain access to the web panel.
- Via valid credentials or vulnerability exploitation.
- Obtain the associated mobile number.
We managed to simulate an attack on our test equipments and we were successful. For point 1, we bruteforced our way in using default credentials. This allowed us to go through and parse router's SMS messages and found one which contained the associated mobile number. The SMS message was sent from the provider.

Going through SMS messages manually to identify the mobile number is not nice nor practical. Thus we ask, can this be automated? The answer is yes and we developed a PoC specific to Huawei routers. The POC is shown below:
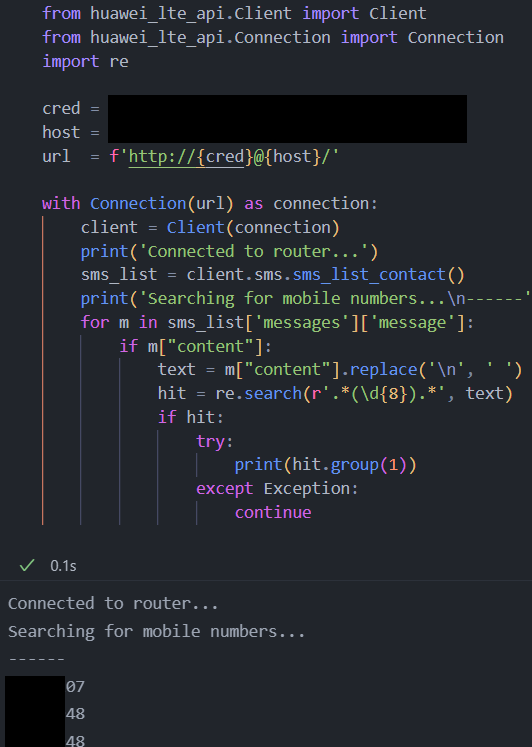
The PoC utilizes an existing open source python library to communicate and interact with supported routers. The library has the ability to retrieve SMS messages from the router after successfully authenticating to it.
The script authenticates to the router, retrieves the SMS messages, and then proceeds with using regex to identify 8 consecutive digits in the SMS messages contents, which represents possible mobile numbers.
Of course, brute forcing credentials can be automated as well. Combining that with mobile number identification via SMS search automation means both requirements needed to obtain a line can be satisfied via a tool. This leads to the attack being scalable.
Note that, sometimes it is possible for a malicious actor to send an SMS message to themselves to obtain the mobile router's number.
Impact
Ability to launch phishing attacks using services which require a mobile number to complete registration. This attack allows malicious actors to launch phishing campaigns from social media/internet messaging accounts registered using victim mobile numbers. Below are examples seen in the wild where threat actors might have used the vector we are discussing in this post.


Mobile Router Settings Analysis
We looked at the settings of our Nighthawk M5 Netgear test router, which is a small portable router powered by a rechargeable battery, to see if it is possible to disable public access administration panel through WAN. And sadly we could not find such an option. Moreover, we could not find any logs of any kind.

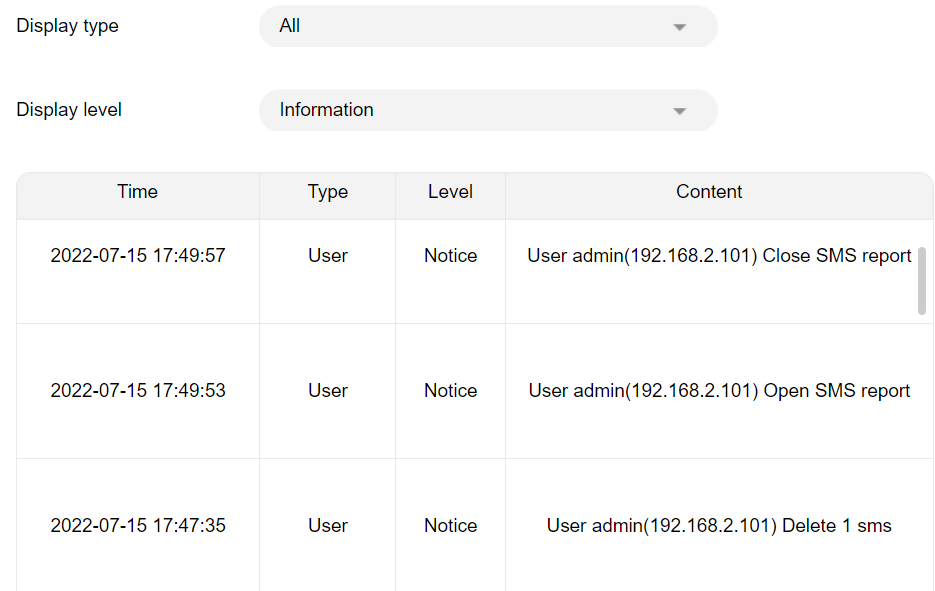
Moving on to our Huawei test router, it a stationary 5G router. To be fair, It is much bigger in size than the Netgear router. This router's administration page had login attempt throttling and audit logs which both did not exist on the Netgear router. However, still we could not find an option to turn off the public facing administration panel.
Mitigations and Recommendations
Recommendations:
- Ensure you go through the mobile router's adminsitration panel to understand what features, capabilities, and settings exist, you do not want to be surprised.
- Enable access and audit logging if possible.
- Use a firewall or network access controls.
Below we list some mitigations:
- Turn off the public facing adminsitration web panel if possible.
- Change the default password of the adminsitration web panel to something complex.
- Ensure the mobile router is up to date.
It would be great if vendors would implement MFA. This makes getting access to the device's administration panel harder.
Further reading
Articles which discussed SMS service abuse in mobile routers:
- https://therecord.media/botnet-abuses-tp-link-routers-for-years-in-sms-messaging-as-a-service-scheme/
- https://www.engadget.com/syniverse-sms-routing-company-hacked-131314113.html
- https://newsreadonline.com/hackers-have-been-hacking-wi-fi-routers-for-5-years-to-send-sms-from-them/
Authors:
Hamad Al Omairah:
- Twitter: @Hamadkuw85
Humoud Al Saleh:
- Twitter: @ma4j0r