Hunting for Leaked Cobalt Strike v4.9 servers
News about a leak of Cobalt Strike v4.9 broke out on 2023-10-09 and there seems to be two versions, one appears to be leaked by an actor that goes by alias "pwn3rzs" and the other one is allegedly available on a Chinese website.
Seems to be spreading around Telegram fast, along with the arsenal kit pic.twitter.com/XVczRlgfa3
— Dominic Chell 👻 (@domchell) October 9, 2023
We got our hands on the "pwn3rzs" leak and started playing around and searching for indicators. We noticed that it contains a script which does minor checks and applies some configurations. Then, it proceeds to run the CS Team Server. The configuration introduced contains several changes but what caught our eyes is generating an SSL/TLS certificate. This certificate is used later by the "Team Server".
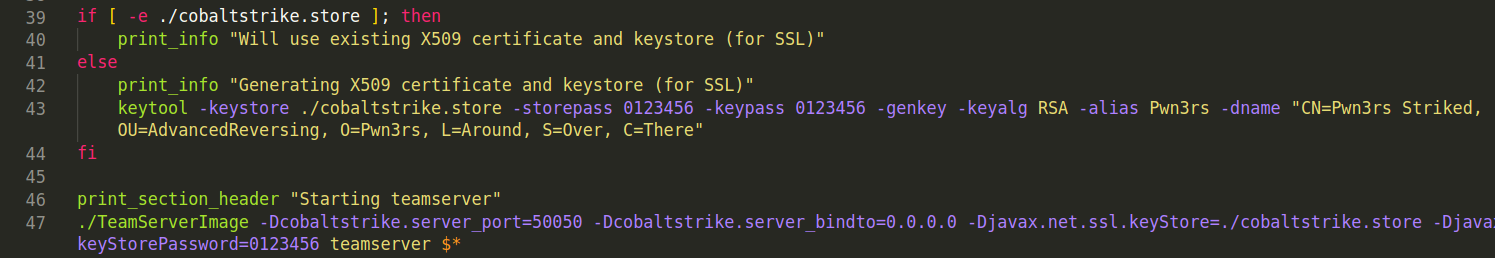
Taking a close look at the parameters passed to the keytool command, we noticed multiple indicators that we can utilize to build detection rules to identify the infra being used by a threat actor who decided to utilize this leaked version of CS without introducing any changes on the configuration (specifically the SSL/TLS certificate parameters)
The indicators we extracted are as follows:
- The "Team Server" will be running at port
50050 - The service on that port will be utilizing the generated SSL/TLS certificate with the following values:
| Field | Value |
|---|---|
| Common Name | Pwn3rs Striked |
| Organization | Pwn3rs |
| Organizational Unit | AdvancedReversing |
| Locality or City | Around |
| State or Province | Over |
| Country Name | There |
We attempted to test our detection rules in the wild and we already got multiple hits:
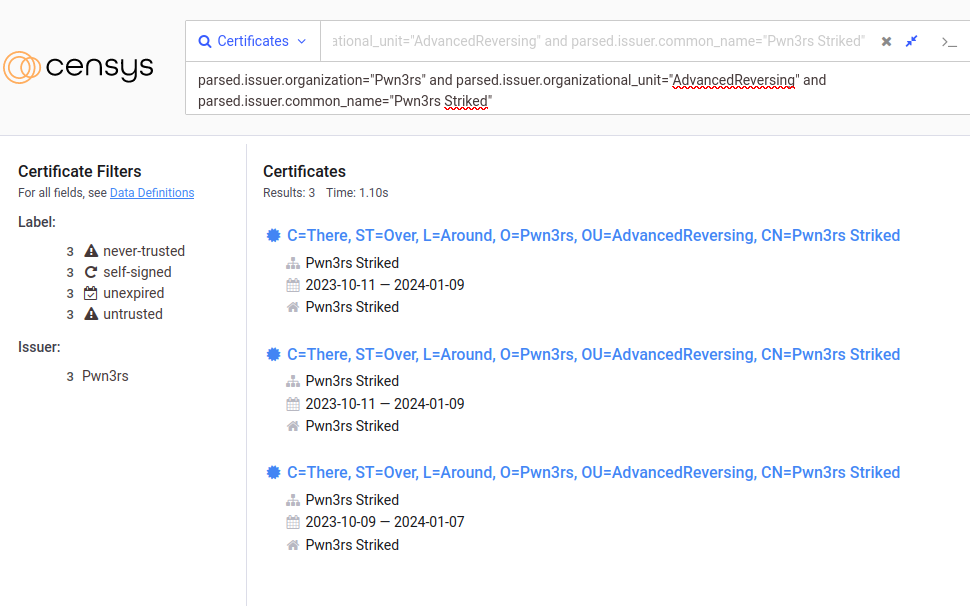
We decided to pivot from identified certificate(s) to corresponding host(s) and found two servers:
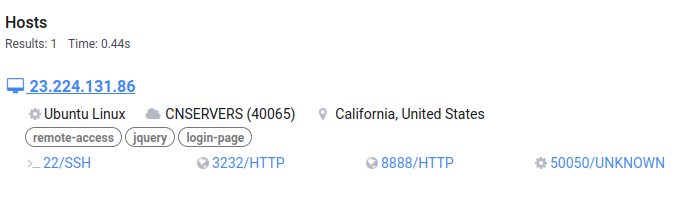
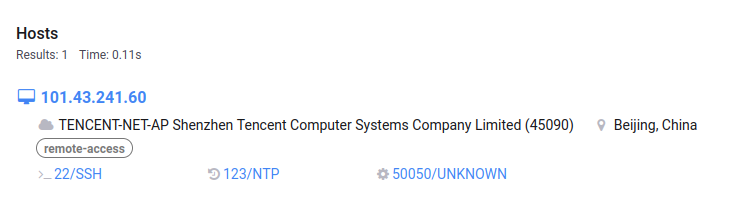
We verified the served SSL/TLS certificate manually and we can confirm it matches the indicators collected from the leak.
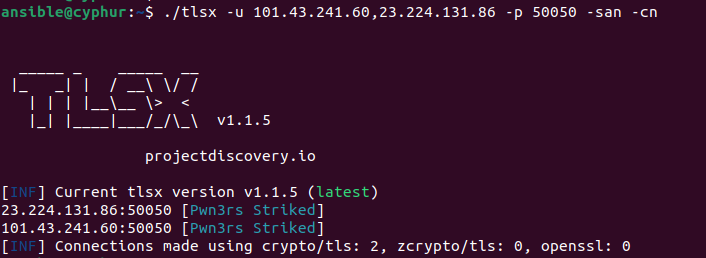
C2 Servers:
- 101[.]43[.]241[.]60
- 23[.]224[.]131[.]86
SSL Certificate Indicators:
| Field | Value |
|---|---|
| Common Name | Pwn3rs Striked |
| Organization | Pwn3rs |
| Organizational Unit | AdvancedReversing |
| Locality or City | Around |
| State or Province | Over |
| Country Name | There |
Leaked File Hashes
| Filename | SHA256 | SHA1 |
|---|---|---|
| CobaltStrike 4.9 Client Only Full Theme uCare@Pwn3rzs.7z | 31a98200d59d412c8621abcec1a54204e873d0cf3ccddb741a0e1bcc90bc91b1 | ac193b5bb51d6fb8067d7d90a8f2a6be76504ce |
| CobaltStrike 4.9 Cracked uCare@Pwn3rzs.7z | 235e31f417f11cff624b3db99ceb35f42ac33c9e78a85a06ec5f084d4604b70a | 6d18b196d16571c4f4e1e30d79ac2591b279bcb |
Authors:
- Humoud Al Saleh
- Majid Alqabandi